The avionics industry is moving more and more towards the use of multicore platforms and applications. While this presents benefits in terms of improved performance, it also presents challenges in terms of meeting specific multicore guidance A(M)C 20-193 and CAST-32A. A major obstacle in meeting this guidance is understanding and quantifying the impact of interference on platform and application behavior. Various strategies are available to mitigate interference from board and chip manufacturers and RTOS vendors. When these strategies are used, their effectiveness must be verified.
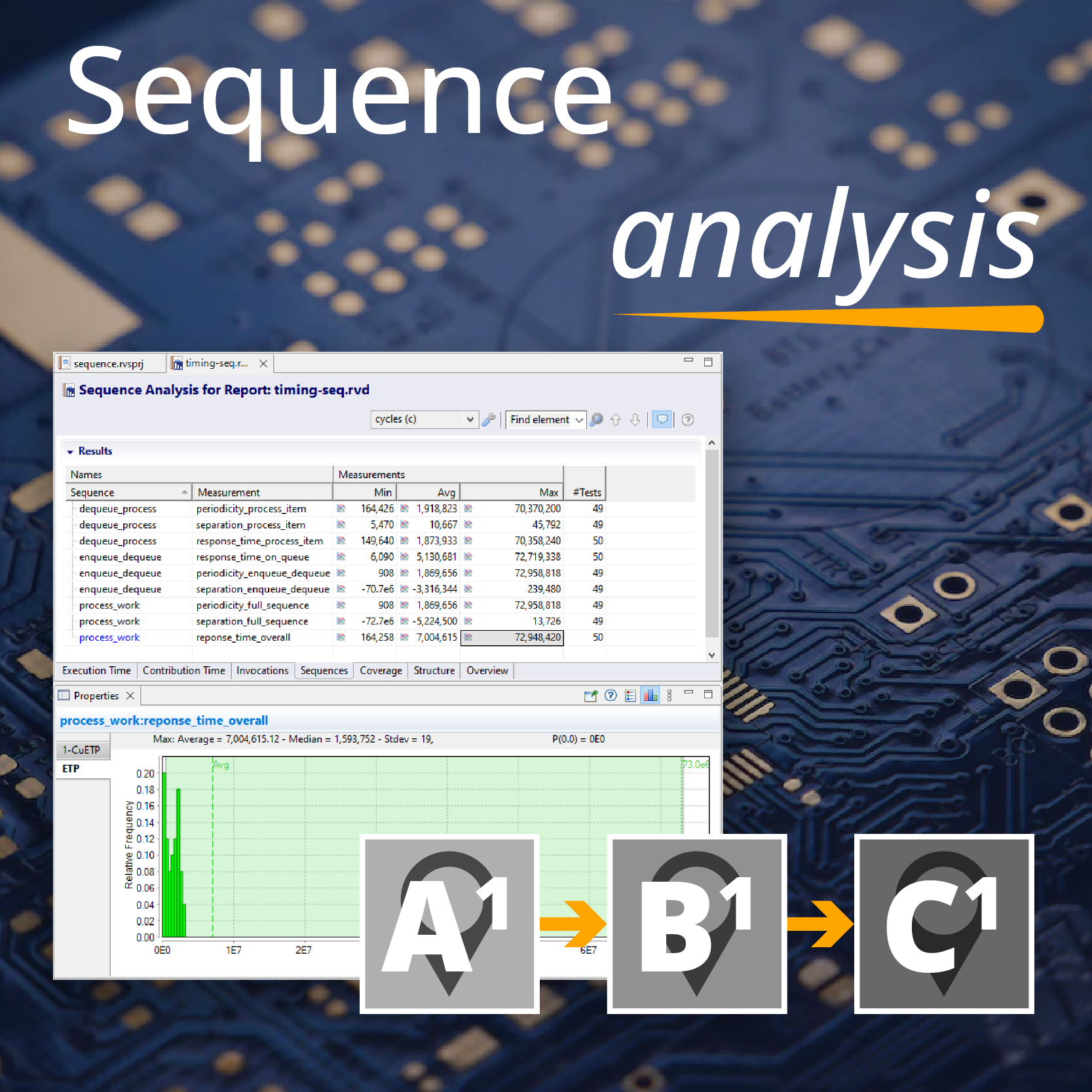
For single core systems, it is relatively straightforward to analyze software timing behavior and put an upper bound on the system’s worst-case timing behavior. For multicore systems, however, this is more challenging. Contention for shared resources such as caches, buses and interconnects in a multicore system increase non-determinism in timing behavior, as the timing behavior of an application accessing a shared resource may depend on whether or not other cores are simultaneously trying to access the same resource, and this isn’t necessarily known. Effects leading to this non-determinism are known as interference, and the channels through which they occur (e.g. a particular shared cache) are known as interference channels (Figure 1).
To comply with A(M)C 20-193 objectives, all interference channels in a system must be considered. Interference channels can be direct (obvious), indirect (non-obvious/obscure), or unknown (undocumented channels that must be discovered). Some channels can be mitigated (either fully or partially) by disabling hardware, imposing constraints on the design (for instance, cache partitioning), or using run-time protection mechanisms (for example bandwidth monitoring or fine-grained locking). Cache partitioning, for example, provides protection from one core/partition evicting the other by making sure no two cores/partitions use the same section of the cache (Figure 2).
While mitigation mechanisms can help reduce required verification effort, verification is still required regardless of which mitigation mechanism is used (MCP_Resource_Usage_3, Figure 3). For example, when an interference channel is fully mitigated by disabling a component, verification is needed to demonstrate that the component is disabled and remains disabled while the software is running. When an interference channel is partially mitigated by design or through run-time protection mechanisms, the effectiveness of the mitigations must be verified to demonstrate that the interference is within acceptable bounds.

After interference channels have been understood and mitigation mechanisms verified, software timing behavior must be analyzed (Figure 3). This must be done in the context of any interference channels that are active in the system (even channels that have been partially mitigated).
Specialist expertise and technology is needed to identify interference channels, verify the effectiveness of mitigation strategies, and analyze execution time behavior for multicore systems in line with A(M)C 20-193 objectives. Rapita’s MACH178 solution supports this end-to-end.
Wanting to learn more about A(M)C 20-193 or CAST-32A certification? Our Multicore DO-178C training courses may be just what you’re looking for.

 SAIF Autonomy to use RVS to verify their groundbreaking AI platform
SAIF Autonomy to use RVS to verify their groundbreaking AI platform
 Hybrid electric pioneers, Ascendance, join Rapita Systems Trailblazer Partnership Program
Hybrid electric pioneers, Ascendance, join Rapita Systems Trailblazer Partnership Program
 Magline joins Rapita Trailblazer Partnership Program to support DO-178 Certification
Magline joins Rapita Trailblazer Partnership Program to support DO-178 Certification
 How to certify multicore processors - what is everyone asking?
How to certify multicore processors - what is everyone asking?
 Data Coupling Basics in DO-178C
Data Coupling Basics in DO-178C
 Control Coupling Basics in DO-178C
Control Coupling Basics in DO-178C
 Components in Data Coupling and Control Coupling
Components in Data Coupling and Control Coupling
 DO-278A Guidance: Introduction to RTCA DO-278 approval
DO-278A Guidance: Introduction to RTCA DO-278 approval
 ISO 26262
ISO 26262
 Data Coupling & Control Coupling
Data Coupling & Control Coupling
 Verifying additional code for DO-178C
Verifying additional code for DO-178C
 DO-178C Multicore In-person Training (Bristol)
DO-178C Multicore In-person Training (Bristol)
 XPONENTIAL 2025
XPONENTIAL 2025
 Avionics and Testing Innovations 2025
Avionics and Testing Innovations 2025
 DO-178C Multicore In-person Training (Fort Worth, TX)
DO-178C Multicore In-person Training (Fort Worth, TX)